A passkey is a FIDO authentication credential based on FIDO standards, that allows a user to sign in to apps and websites with the same process that they use to unlock their device (biometrics, PIN, or pattern). Passkeys are FIDO cryptographic credentials that are tied to a user’s account on a website or application.
Passkeys support in upcoming Keycloak release (26.4)
September 16 2025 by Peter Skopek
Passkeys have been available in Keycloak since version 23.0.0 as a preview feature. We are happy to announce official support for passkeys in upcoming Keycloak 26.4.0.
What is passkey?
Definition from FIDO Alliance
What’s new?
Passkeys are now seamlessly integrated to Keycloak using both conditional and modal UI. There is no need to modify default browser flow to use passkeys. Passkeys support is not enabled by default. It needs to be enabled in the WebAuthn Passwordless Policy (Authentication → Policies → Webauthn Passwordless Policy).
There is new Conditional - credential authenticator that checks if a specific credential type (passkey) has been used during the authentication process. It is added to the default browser flow to skip 2FA in case a passkey was used to log in as the primary credential.
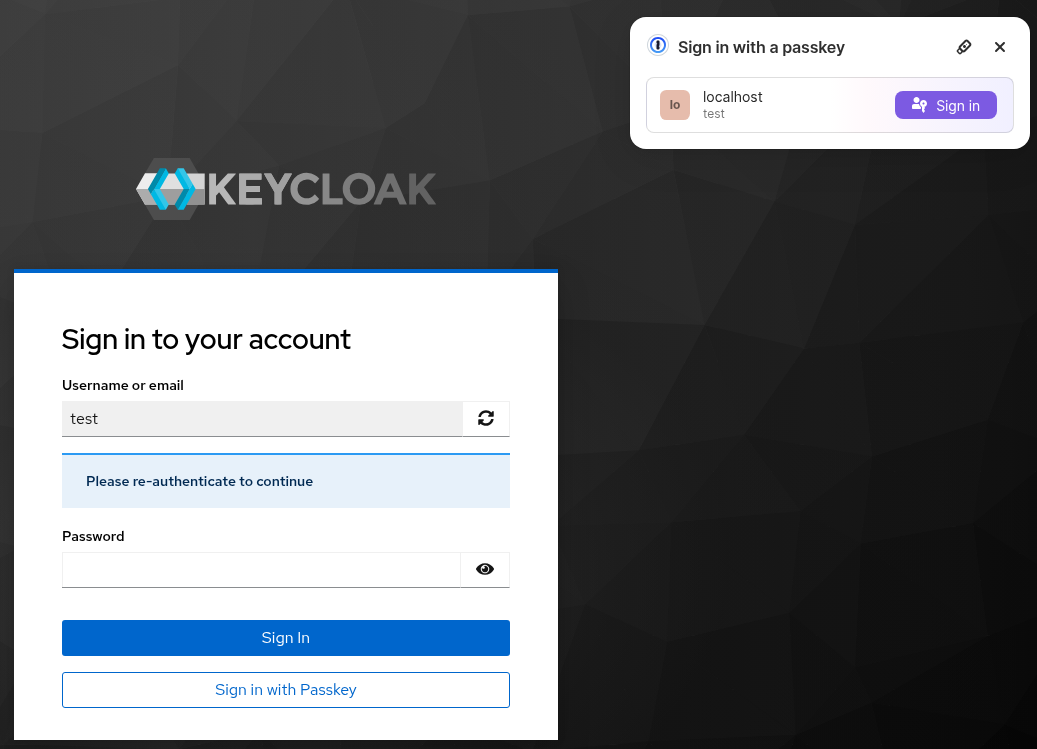
Further quite hidden passkey support is also in the re-authentication form, where users can choose passkey as well as password.
For more information check Keycloak Server Administration Guide.
A few examples
Let’s start form the fresh Keycloak database. The first steps are obvious ones.
-
create admin user
-
create one test user
-
enable passkey support in (Authentication → Policies → Webauthn Passwordless Policy)
-
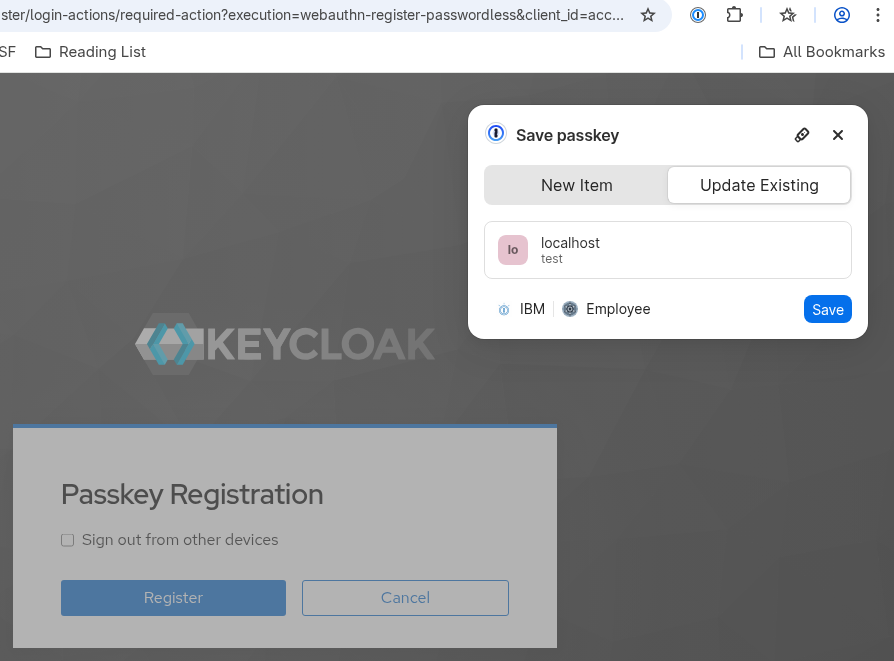
set default required action in (Authentication → Required actions → Webauthn Register Passwordless)
(This step is not necessary, one can use Account Console to register a passkey.)
No need for any other changes.
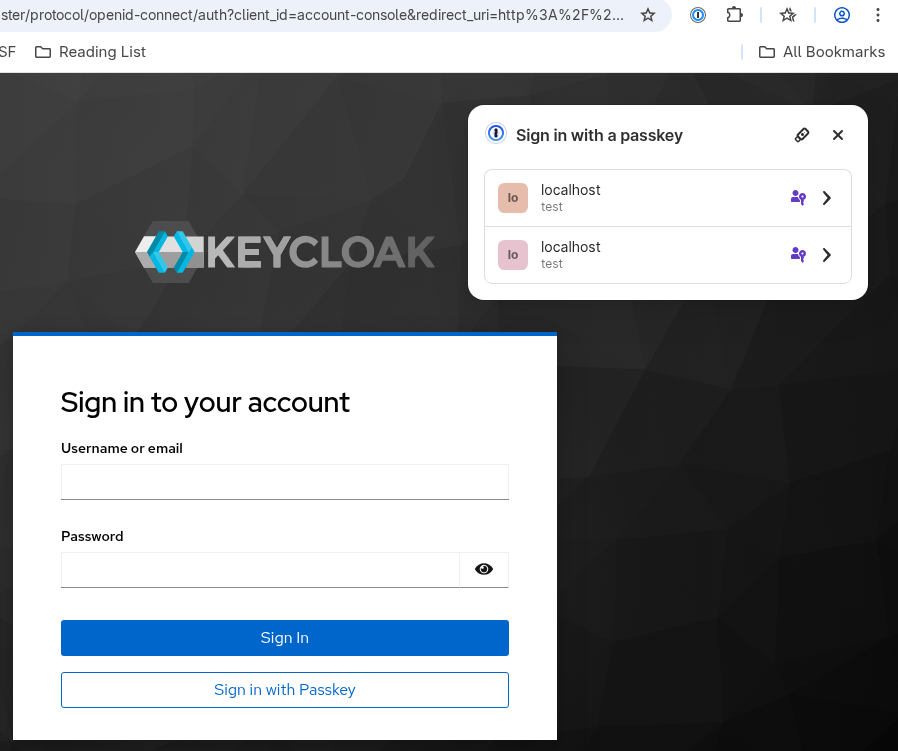
Conditional UI
Conditional UI is displayed when other components of the platform supports this UI style and username input field is present. It can be achieved for example on Linux using Google Chrome browser and 1password password manager with Chrome extension for 1password.
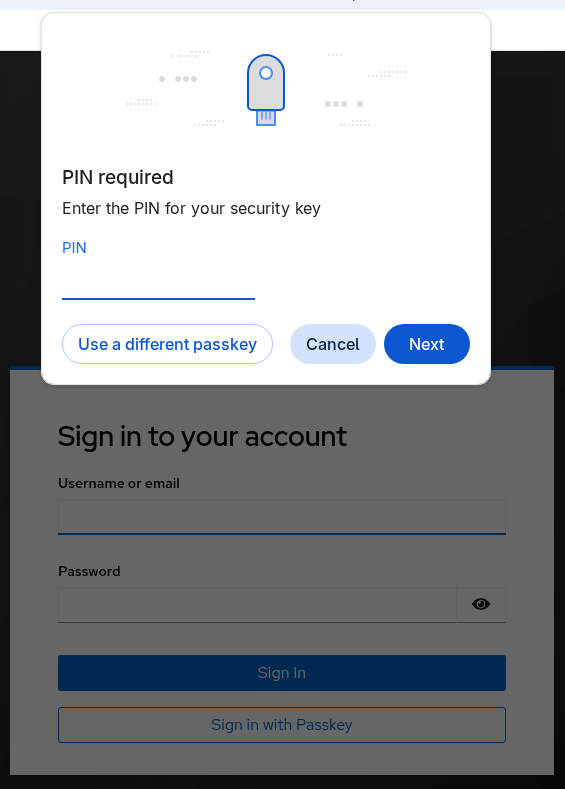
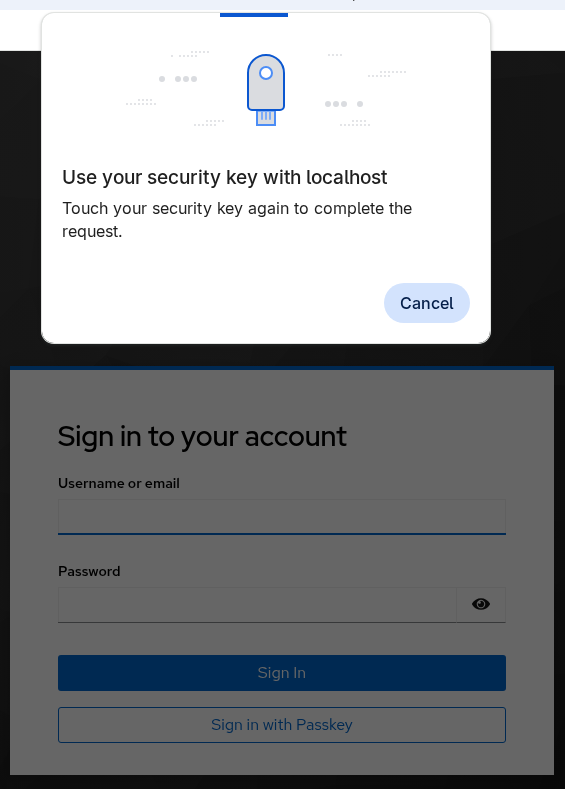
Modal UI
Modal UI is an older style and it is used mainly with hardware keys asking for PIN or biometric (such as Yubikeys). It is directly supported in all major browsers. This style of UI is displayed on browser screen when username input field is present (same situations than conditional) but also when the username is already selected and password is requested (re-authentication for example). The modal UI is initiated clicking the button labelled Sign in with Passkey.
The modal UI can also be slightly different depending on data stored in your hardware key.
Conclusion
All examples here show the passkeys usage with minimal configuration. There are much more options to change behavior of passkeys in Keycloak authentication. For more information see Keycloak Server Administration Guide.
Let us know of possible issues or what you like, please. We are looking for different combinations of operating systems, browsers, password managers and hardware keys. All issues should be reported at our project. Thank you in advance.